PHP remains one of the most widely used server-side scripting languages for web development. However, poor security practices can expose your application to serious vulnerabilities, leading to data breaches, financial loss, and reputational damage. Here are five critical PHP security mistakes that developers must avoid to ensure robust application security.
1. Failing to Sanitize User Input
User input is one of the biggest sources of security vulnerabilities in PHP applications. Failing to properly validate and sanitize user input can lead to SQL injection, cross-site scripting (XSS), and other malicious attacks.
How to Fix It:
- Use prepared statements and parameterized queries to prevent SQL injection.
- Escape user inputs using functions like
htmlspecialchars()to prevent XSS attacks. - Implement strong validation rules with PHP’s built-in filtering functions like
filter_var().
2. Using Outdated PHP Versions
Many developers continue to use outdated PHP versions that are no longer supported. These versions do not receive security updates, making them easy targets for hackers.
How to Fix It:
- Regularly update your PHP version to the latest stable release.
- Monitor the official PHP support lifecycle and plan upgrades accordingly.
- Use dependency management tools like Composer to keep libraries updated.
3. Improper Error Handling
Revealing detailed error messages in production environments can expose system vulnerabilities to attackers. Stack traces, SQL errors, and file paths can provide hackers with useful information for exploiting your system.
How to Fix It:
- Disable error reporting in production (
display_errors = Offinphp.ini). - Log errors instead of displaying them using
error_log(). - Use try-catch blocks to handle exceptions securely without exposing sensitive information.
4. Weak Authentication and Session Management

Weak password policies, improper session handling, and unencrypted data storage can make applications vulnerable to unauthorized access.
How to Fix It:
- Enforce strong password policies and use
password_hash()for secure storage. - Use HTTPS to protect session data from man-in-the-middle attacks.
- Implement session timeout and regeneration mechanisms to prevent session hijacking.
- Restrict session cookies to HTTP-only and secure mode (
session.cookie_httponly = 1andsession.cookie_secure = 1).
5. Hardcoding Sensitive Information
Storing API keys, database credentials, or other sensitive information directly in the codebase is a serious security risk. If the source code is exposed, attackers can gain access to critical system resources.
How to Fix It:
- Store sensitive data in environment variables using
.envfiles. - Use configuration files located outside the web root directory.
- Implement secure secrets management tools like AWS Secrets Manager or HashiCorp Vault.
Expert PHP Security Solutions by Dev Centre House Ireland
Avoiding these PHP security mistakes is crucial for building secure and resilient web applications. At Dev Centre House Ireland, we specialize in PHP development and security best practices, helping businesses safeguard their applications against cyber threats. Whether you need a security audit, development support, or consulting, our team is ready to assist.
Learn more about our PHP services: https://www.devcentrehouse.eu/en/technologies/back-end/php
PHP 8+: 8 Game-Changing Features Every Developer Should Know

PHP 8+ has introduced several groundbreaking features that enhance performance, improve syntax, and provide better error handling. Whether you’re building web applications or enterprise solutions, understanding these updates can help you write more efficient and maintainable code. Here are eight game-changing features every PHP developer should know.
1. JIT (Just-In-Time) Compilation
One of the most significant improvements in PHP 8 is the introduction of JIT compilation. JIT compiles PHP code at runtime into machine code, improving execution speed and making PHP more competitive with languages like Python and Java. This enhancement benefits CPU-intensive applications like image processing, data analysis, and machine learning.
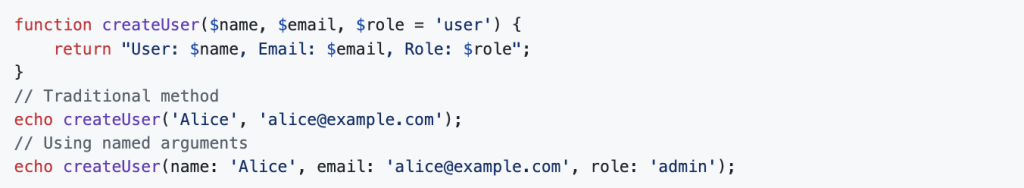
2. Named Arguments
PHP 8 introduces named arguments, allowing developers to pass values to functions based on parameter names rather than position. This improves code readability and makes function calls more intuitive.
Example:
3. Attributes (Annotations)
Attributes (also known as annotations) provide a native way to add metadata to classes, methods, and properties, eliminating the need for docblock-based annotations.
Example:

This feature enhances code readability and simplifies framework-based development in Laravel and Symfony.
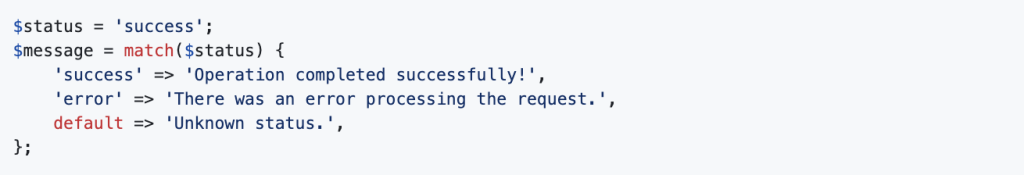
4. Match Expression
PHP 8 introduces the match expression as a more powerful and safer alternative to switch statements. Unlike switch, match ensures strict type comparisons and returns a value.
Example:
This makes conditional logic more concise and predictable.
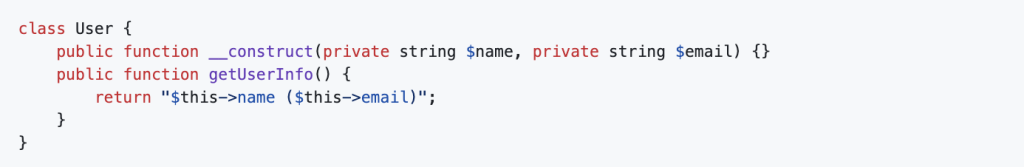
5. Constructor Property Promotion

PHP 8 simplifies class property initialization with constructor property promotion, reducing boilerplate code.
Example:
This eliminates redundant property declarations, making classes cleaner and easier to read.
6. Nullsafe Operator
Handling null values in PHP has always required extensive checks. PHP 8 introduces the nullsafe operator (?->), which prevents null reference errors.
Example:

Instead of throwing an error, this returns null if any method in the chain fails.
7. Union Types
PHP 8+ allows functions to accept multiple data types using union types, improving type safety.
Example:

This feature enhances flexibility while maintaining strict type enforcement.
8. Weak Maps
Weak maps allow objects to be garbage collected when no longer in use, improving memory management and performance in long-running scripts.
Example:

This is particularly useful for caching and dependency injection scenarios.
Elevate Your PHP Development with Dev Centre House Ireland
Harness the full potential of PHP 8+ with expert development services from Dev Centre House Ireland. Our experienced PHP developers leverage cutting-edge features to build robust, high-performance applications tailored to your business needs. Get in touch with us to elevate your backend solutions!
